5 Effective Ways to Acknowledge Australian Data Privacy & Cybersecurity Reforms

Do you know you are never safe on the internet? In this modern, digital era, data drives vital business functions and decisions, transforming customer interactions and business success.
However, these advancements are creating an alarming number of cybersecurity challenges derived from the reliance on online data. Like other businesses worldwide, Australian businesses face the jeopardy and danger of cyber threats.
The latest and perhaps most decisive death blow to the Australian cybercrime scene came in 2022, when, over a three-week tenure, the personal data of around 10 million Optus and Medibank customers fell into the hands of cyber criminals! The impact created shockwaves that compelled the Australian Government to announce the development of a new cybersecurity strategy in the country that amends the major security laws and codes.
With these reforms in place, protecting your organisation from cyberattacks and online data breaches is imperative. Below, we explore some online data issues, discuss five effective ways to fortify your business against cyber threats, retain customers, and protect your business data and reputation.
Table of Contents
- Some Prevalent Forms of Cyber Security and Data Breaches
- Identity of Cybercriminals
- The Protective Measures
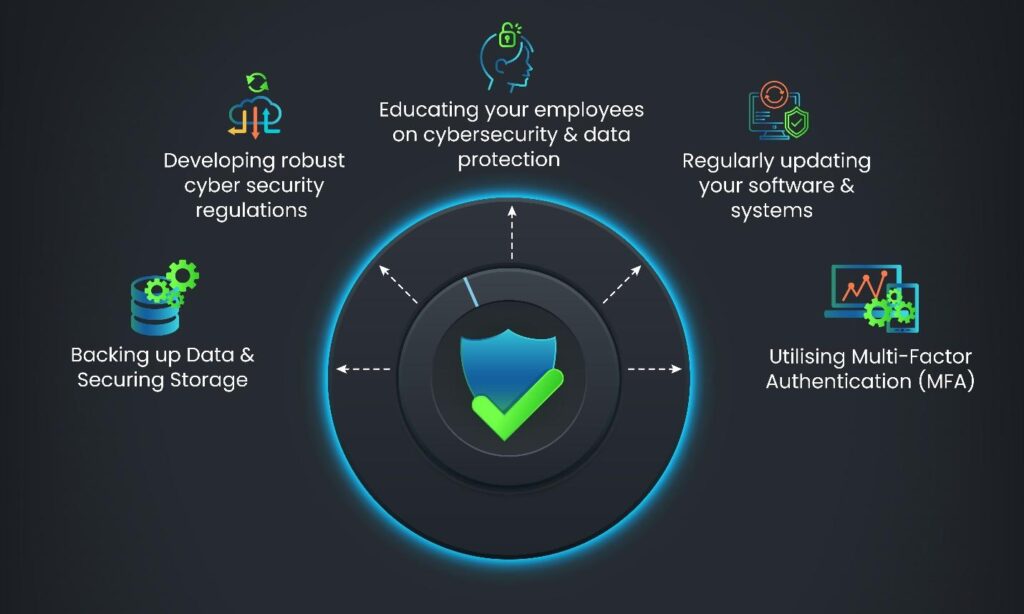
- Regularly updating your software and systems
- Educating your employees on cybersecurity and data protection
- Developing robust cyber security regulations
- Backing up Data and Securing Storage
- Utilising Multi-Factor Authentication (MFA)
- Additional Steps to Secure Organisation and Business Data
- Going Forward into The Future
Some Prevalent Forms of Cyber Security and Data Breaches
Data breaches occur in multiple ways. Some go unnoticed and may not feel too big a deal. But others can create severe impacts and disastrous consequences, especially for business organisations. From malfunctioning systems to mammoth financial losses, these online data breaches can wreak havoc in minutes without warning.
Some common types of data privacy breaches globally are:
- Acquiring access to your confidential data via your staff or clients.
- Introducing malware like viruses, ransomware, and spyware into computer systems.
- Accessing unauthorized information on hardware, computers, and mobile devices.
- Compromising third-party systems
- Harming your technology or website through an attack.
- Spamming through emails containing malicious content or malware
In 2022, the Australian Cyber Security Centre (ACSC) reported over 76,000 cybercrime incidents, showing an increase of nearly 13 per cent from 2021. Among them, ransomware topped the list of cyber threats the criminals used, impacting every sector of the economy.
Identity of Cybercriminals
So, who could be a Cybercriminal? According to Australian Cybersecurity agencies, the attacks can be carried out individually or as a group. Though majorly deliberate, the attacks can sometimes be unintended or a mistake.
As business owners or corporate professionals, you should know that the threats can come from any or all cylinders like:
- Criminals looking to illegally access your hardware and data to extract money or disrupt your business functions.
- An ill-intended or ignorant client trying to compromise your information.
- Business or industry competitors trying to gain the upper hand in the market. This mal-intended tactic is also called insider trading, in general, and laws enforcers can penalise corporations and the offenders with huge fines and long jail terms.
- An employee or group of employees who mistakenly or intentionally compromise your data.
We suggest you keep a close eye and surveillance on such matters to avoid data security threats and legal issues.
The Protective Measures
Keeping your business and yourself immune to cybersecurity threats and data breaches may be vital to sustaining in the market. Whether you build a powerful cybersecurity team internally or augment IT staff or resources externally, you must evaluate how secure your business is from cyber threats.
To avail online security expertise, you can contact IT consulting and digital service firms like APACON to extend their expert information security solutions for your online perils. APACON assists you in analysing the cyber risks, drafting cyber policies according to the latest Government regulations and reforms, and setting up enhanced resilience against cyber-attacks and data breaches.
Let’s now learn about five effective and tested ways to protect your business from cyber data breaches and attacks, in general:
Regularly updating your software and systems:
Failing to update software and operating systems opens the floodgates for cyber-attacks. Hackers and cybercriminals exploit these vulnerabilities in outdated software and gain unauthorised access to your business data with just a few clicks and type-ins. System administrators must ensure that all software applications and systems are regularly updated with the latest security patches. Especially if you use antivirus software, ensure it’s an authenticated copy and up to date. Keep auto-update turned on whenever possible to ensure you never miss essential updates.
Educating your employees on cybersecurity and data protection:
Your employees play a substantial role in protecting your business from cyber threats. One way to accomplish this is by educating your staff and employees about cybersecurity. This step ensures your loyal employees take proactive measures to prevent data breaches or attacks that may compromise your company’s sensitive information.
You can facilitate regular training and educational programs covering various aspects of information security, like data privacy, network security, secure coding practices, password management, etc.
We suggest you encourage your team members and employees to set strong, unique passwords and refrain from clicking on suspicious links or accessing files from unknown internet sources. APACON thrives in making business professionals aware of information risks and data breaches by organising training programs and workshops conducted by industry experts. The awareness programs transform your employees into your first line of cyber defence.
Developing robust cyber security regulations:
Like a company Code of Conduct (COC), you should also develop cyber security codes of practice or guidelines to help your staff understand and maintain acceptable ways of handling and using data, devices, emails, and internet sites. You may also restrict access to various internet websites on their office computers if needed.
You can also create a comprehensive incident response plan outlining the measures to adopt in a cyber-attack. It will also boost your chances of surviving data attacks if you assign roles and responsibilities to key personnel for protocols to handle such unwanted situations efficiently.
Backing up Data and Securing Storage
Whether caused by a cyber-attack or a hardware failure, losing data can badly disrupt and affect your business. You should implement a vigorous data backup plan, which regularly backs up official and business data with bulletproof security.
You can use encrypted cloud storage services for additional support to prevent unauthorised access to data in case of untraced virus attacks or hacks. APACON excels at helping clients migrate to highly secure and affordable cloud storage services to safeguard them from ransom or malware attacks and possible data breaches.
Utilising Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) requires users to provide a mixture of information they know or already have. These units of information are usually the following:
- A physical token
- Fingerprints or biometrics
- An Authenticator Application (like Microsoft or Facebook’s)
- An email that is sent to you to verify log in
- An SMS is sent to your mobile to type in a PIN code or One-time Password (OTP).
As this method has more than one step, it offers an extra layer of protection to your business accounts or pages. Entering multiple factors like passwords, fingerprints, or one-time codes to enter an online account or page significantly reduces the risks of unauthorised access.
For instance, Australian Cyber Security Center (ACSC) is running campaigns that foster and encourage all individuals and businesses to implement MFA to protect against ransomware and cyber data breaches.

(Image1-Source: https://www.cyber.gov.au/sites/default/files/2023-04)
Additional Steps to Secure Organisation and Business Data
In addition to the five measurements shared above, you should also emphasise ensuring the following:
- Secured Network with Firewalls and Encryptions: Secure your business network by investing in effective and powerful firewalls and encryption technologies to defend data transmission over undesired public networks. You can utilise network segmentation (a method that segments a network into smaller sub-networks for improved security and control) to streamline and limit access to sensitive information. This strategy noticeably reduces the impact of a cyber-attacks.
- Regular Online Security Checks or Audits: Frequent security audits assess your business’s cybersecurity condition and identify possible loopholes. Onboarding cybersecurity experts or professionals, internally or externally, to perform comprehensive inspections of your systems, applications, and processes keeps your data security updated and strong. Consulting firms like APACON offer a range of audits to ensure security policies meet regulatory requirements, no vulnerabilities exist in the client’s systems, appropriate information is available all-time, and data is protected with the best-in-class tools.
Going Forward into The Future
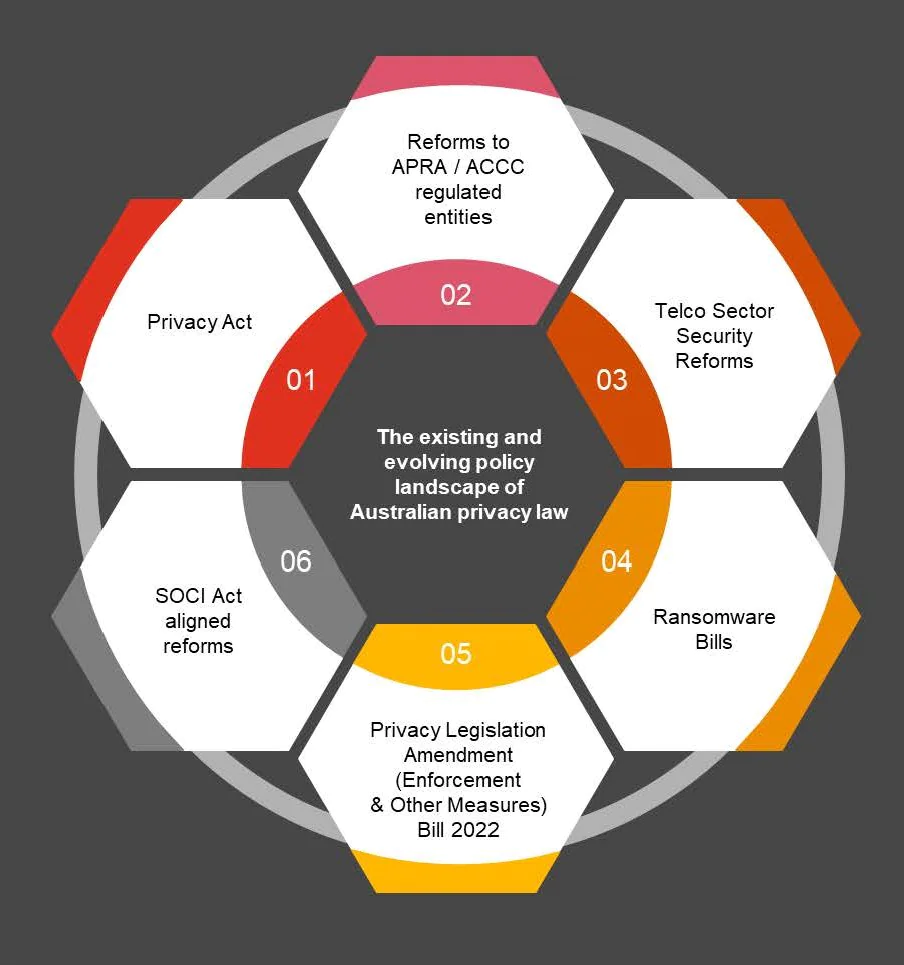
(Image 2-Source: https://www.pwc.com.au/legal/publications/)
The unchecked data leaks and cybercrimes in Australia and worldwide forced the Government to announce a new cybersecurity strategy that impacts and amends multiple data privacy and cyber security regulations.
As cybercrime becomes more complex and diverse, new challenges will arise. To address and tackle this concerning situation, Australia’s cybersecurity regulations must function effectively and efficiently to protect against cybercrimes.
And you, as a business owner or professional, can secure data by keeping software updated, educating employees, employing MFA, backing up data, securing your network, facilitating regular audits, and having a robust cyber security plan. Remember, long-term investment in cybersecurity shows your commitment to protecting your customers and their sensitive data, alongside solving their pain points.
To round off, a Visual Summary of the 5 Data Privacy Measures discussed here is presented as follows: